Ensuring SS7 Network Security
Welcome to another November 2018 issue of GL's Newsletter discussing vulnerabilities in SS7(SIGTRAN) networks and insights into GL’s MAPS™ SS7 solution to generate these SS7 attacks by simulating various SS7 messages and manipulation of SCCP, MAP, CAP parameters.
GL’s MAPS™ solution simulates illegitimate SS7 (SIgtran) messages in order to test active filters at SS7 Firewalls, STPs, and other network nodes to check the attacks as per ‘SS7 Security Network Implementation Guidelines .
In addition, GL’s Network Monitoring and Surveillance Solution can be deployed at probe level to monitor the SS7 traffic.
Overview
The mobile communication infrastructures have evolved from traditional circuit-based networks into broadband and IP-based networks. In this process SIGTRAN was proposed for carrying SS7 PSTN signaling over IP. The vulnerabilities in SS7 signaling protocol inherited to SIGTRAN allowing intruders to easily intercept mobile networks. Although large scale attacks are not common, still they may significantly impact individual subscribers with financial loss, confidential data leaks, and/or disruption of communication services (voice and sms). As per “SS7 and SIGTRAN Network Security” high-level recommendations, there is a serious need for a complete SS7 traffic monitoring and analysis system to check if there are real SS7 attacks. And a solution to simulate SS7 illegitimate messages in order to create filters at various check-points in the network and block such messages.
Real-time SS7 network attacks include tracking a subscriber’s location, data theft, eavesdropping, text interception, unstructured supplementary service data (USSD) forgery requests, and voice call redirection. At a network level such attacks can reduce the availability of a mobile switch leading to denial of service for certain subscribers or the whole network. For example, an intruder can send, intercept and alter SS7 messages by executing various attacks against mobile networks and their subscribers.
Such security challenges require significant testing, monitoring and troubleshooting.
GL offers a complete test solution includes Message Automation & Protocol Simulation (MAPS™),for SS7 Sigtran protocol which can be easily customized to simulate real-time fraud scenarios addressing critical attacks. And NetSurveyorweb™ monitoring system supporting operators, and service providers to constantly monitor network traffic and detect fraudulent activities.
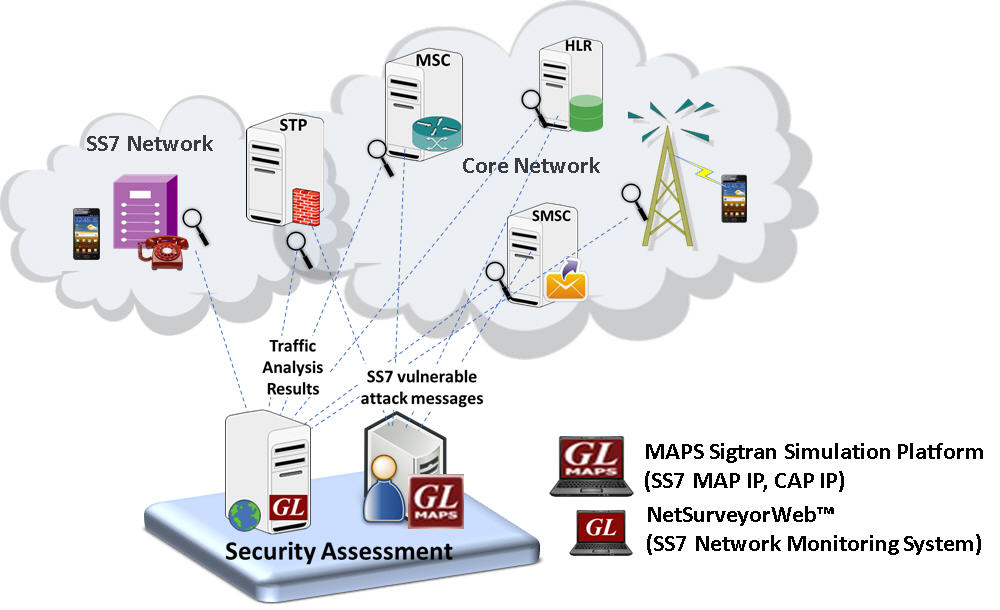
GL's Analysis and Simulation Solution
GL’s Solution
Simulation Test Solution
One of the main recommendations to prevent security attack, is to deploy STP or SS7 Firewall at the network borders and filter out fraudulent SS7 messages from expected nodes. For all SS7 MAP/CAP messages, filtering features can be deployed in different Terminating network nodes, including HLR, MSC, SGSN and also SMSC, EIR, GMLC, gsmSCF.
GL’s MAPS™ (SS7 MAP/CAP) test platform supports inbuilt pre-processing tools that allow the users to customize the messages with protocol specific parameters and create custom scripts to perform real-time fraud scenarios addressing some critical attacks.
Solution defines various features used to implement SS7 MAP/CAP messages filtering on different functional nodes. Commonly, fraudulent attacks are performed by correlating various addresses.
- SS7 messages coming from the interconnection points with an SCCP Calling Party Address (i.e. the calling GT) and a Point Code (i.e. Called GT) not belonging to the same network
- MAP/CAP layer by altering, request and response message parameters, such as, MSISDN (Mobile Subscriber Integrated Services Digital Number), IMSI (International Mobile Subscriber Identity), location, key, Op Code, CgGT (Global Title), and USSD in order to manipulate the services.
Few of the proposed MAP/CAP screening (Op, CgCT, GT, IMSI) feature required to be implemented to block / filter fraudulent messages are as listed below:
| MAP Msgs | CAP Msgs |
|
|
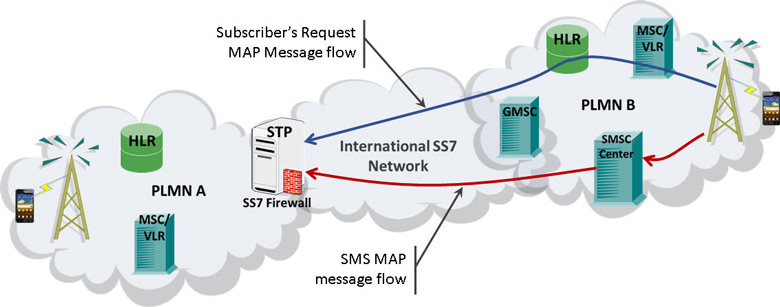
In the following SS7 firewall typical deployment example scenario, the attack is based on requesting the Mobile Switching Center (MSC) Visitor Location Register (VLR) address, and the IMSI. In mobile networks, subscribers are identified by the International Mobile Subscriber Identity (IMSI), which is considered confidential information. GL’s MAPS™ simulating the security assessment node, generates "MAP_provideRoamingNumbering" request message, which carries subscriber’s information required for further routing of the message. At STP/SS7 Firewall, the MAP screening feature mainly checks for the source of the MAP message. When the authenticity of the HLR fails at the firewall, the source is considered as spoofed source node and the messages are filtered.
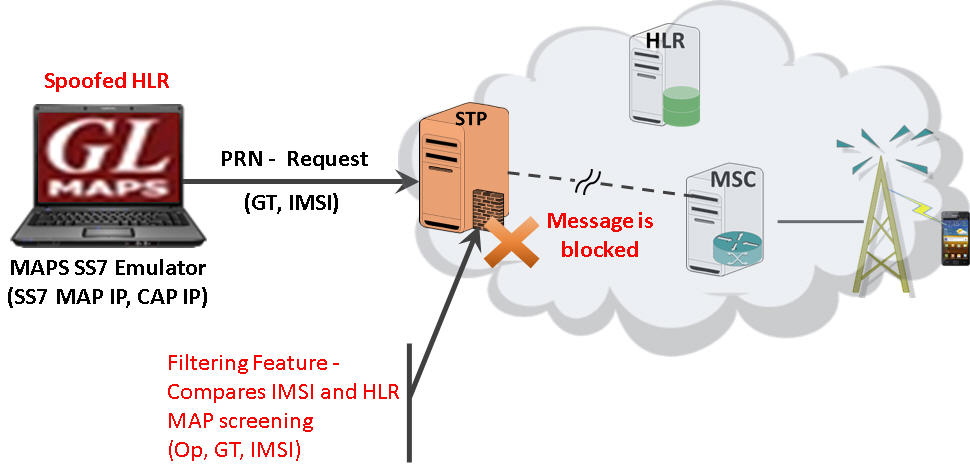
Subscriber Information Retrieval Scenario
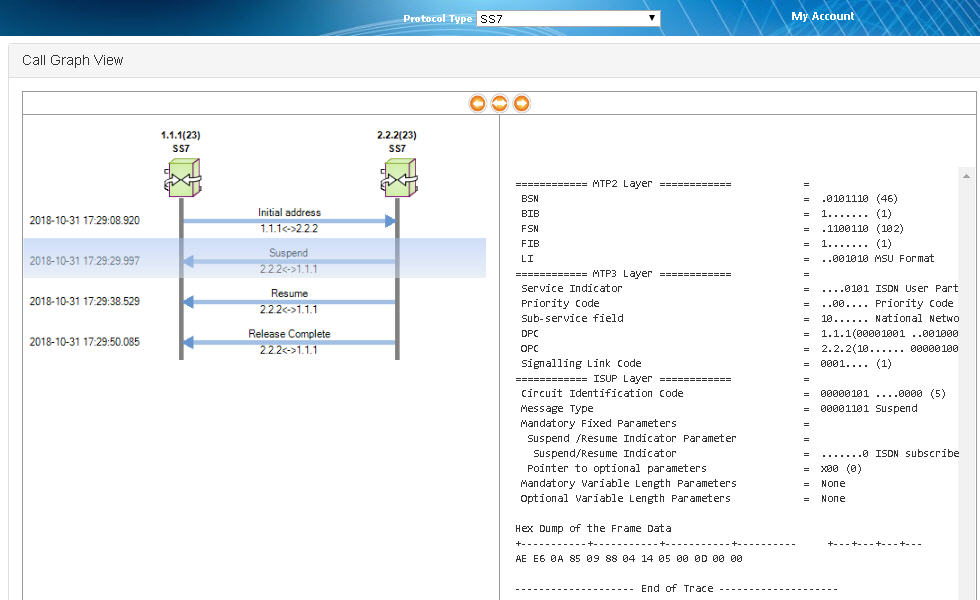
The following screen shot depicts the provideRoamingNumbering message sent from MAPS™ (acting as HLR node) towards the network (MSC) requesting for Subscriber’s GT (Calling & Called Number), and IMSI details.
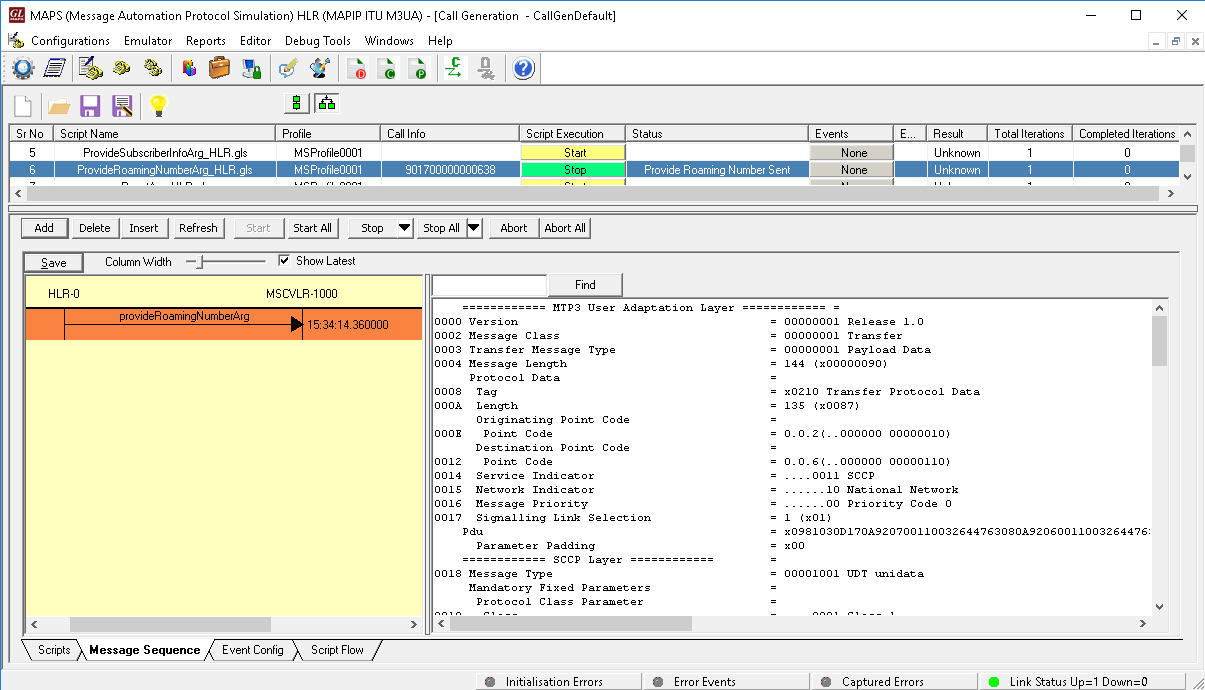
MAPS™ simulating Provide Roaming Number Procedure
Monitoring System
The network security experts recommend monitoring the SS7 traffic for detecting and reporting un-lawful activities, identify fraudulent calls, data retention, targeted surveillance, and study usage patterns.
Generally, methods deployed to perform fraud detection, is to use monitoring tools non-intrusively. GL’s capture, monitoring, and filtering tools can help to identify and drill-down to the “calls-of-interest” or “fraudulent calls”.
The NetSurveyorWeb™ Lite along with Protocol analyzer provides a cost effective and simple plug & play web-based surveillance system that can be distributed at probe level. The network monitoring systems facilitate real-time analysis, historical storage, retrieval, querying, and display of Call Detail Records (CDRs) by non-intrusively connecting to TDM, Optical, or IP networks. Currently supported protocols include LTE, IMS, UMTS IuCS, UMTS IuPS, VoIP (SIP, SIGTRAN, H.323, MAP, CAP, MGCP, MEGACO), SS7, ISDN, CAS, TRAU and GSM.
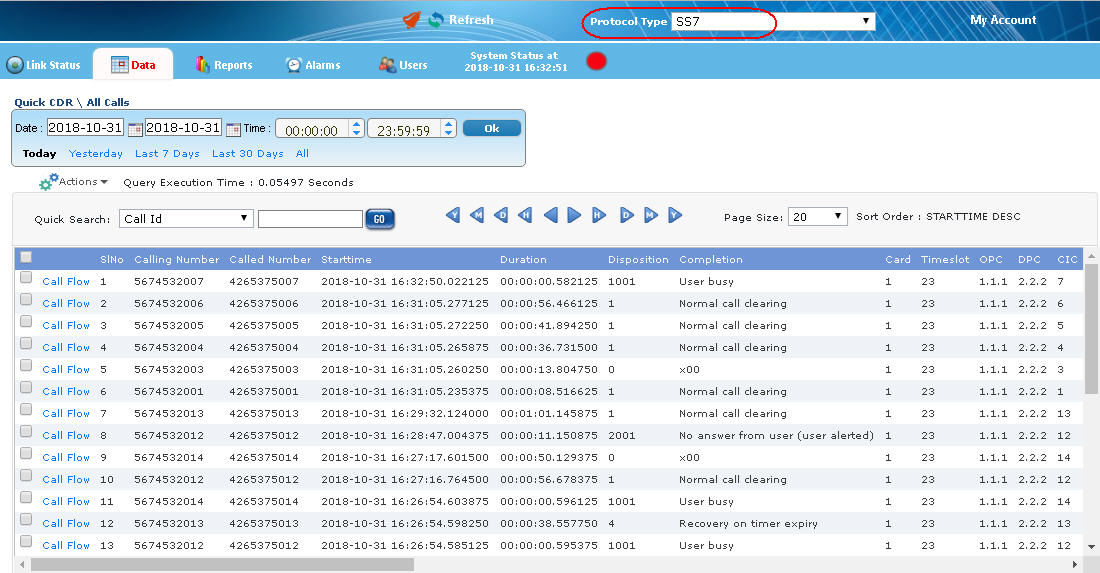
The real-time data view provides visibility into each individual call. Each call can be investigated based on call control, signaling and traffic parameters. Flexible filtering can help organize and identify “Calls of Interest”. In addition, call data records along with the associated call-flows is also available.
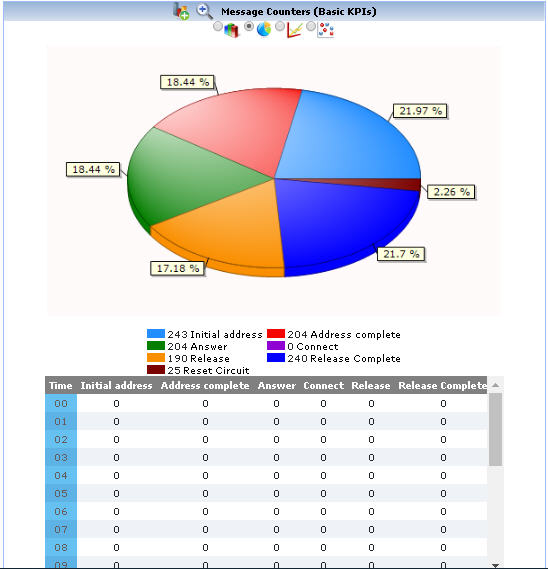
Customized report generation of the captured traffic over the entire network is also possible. Reports are also available in the form of Bar Graph, Pie Chart, Dot Graph, or tabular format for each of the plotted graph.
 Back to Newsletter Index Page
Back to Newsletter Index Page